Microsoft Active Directory is Foundational
Active Directory (AD) is the foundation of IT, cyber security and privileged access at 85+% of organizations worldwide.

Active Directory is the Heart of Privileged Access
Active Directory is the heart of Identity and Access Management (IAM), Privileged Access Management (PAM) and Zero Trust worldwide.

Privileged Access Assessment in AD is Paramount
The "Keys to the Kingdom" and the keys to every asset lie in AD so knowing exactly who has what privileged access in AD is paramount.

We are Paramount Defenses
Microsoft Active Directory is the foundation of cyber security and privileged access at 85% of organizations worldwide.
Founded by former Microsoft Program Manager for Active Directory Security, we possess unrivaled expertise, IP and capability in the top two most critical areas of cyber security - Active Directory Security and Privileged Access.
We uniquely empower organizations worldwide to accurately assess and lockdown privileged access in Active Directory, which is absolutely essential for attaining and maintaining least privilege access (LPA), a cardinal tenet of Zero Trust.

What We Do
In a nutshell, we uniquely enable organizations worldwide to operate secure foundational Active Directory infrastructures by uniquely enabling and empowering them to be able to accurately assess and lockdown access in Active Directory.
Organizations that operate on Active Directory do not have to relinquish* their operational autonomy or privacy.
* As long as an organization operates on Active Directory, it retains its operational autonomy and privacy.
The day an organization transitions its primary identities over to a third-party (e.g. an IDP in the Cloud)
is the day it will have relinqushed both, its operational autonomy and organizational privacy, forever
and taken on an eternal mission-critical dependency on an external third-party.

We uniquely empower organizations to accurately
assess and lockdown privileged access in Active Directory
Today, at organizations worldwide, at the heart and foundation of hybrid and on-prem IT networks lies Active Directory.
At these organizations, all primary identities (domain user accounts), hosts (domain-joined computers) and groups are stored and managed in Active Directory (AD), and secured by AD security permissions that collectively determine who has what privileged access on them.
It is impossible for organizations to secure themselves or to attain Zero Trust without being able to attain and maintain least privilege access in AD, which requires accurately assessing "Who has what privileged access in AD?", which is very difficult and cumbersome.
Our Microsoft-endorsed Gold Finger solution uniquely empowers organizations operating on AD to accurately assess and lockdown exactly who has what privileged access where and how in AD, so they can attain and maintain least privilege access (LPA) in AD, and attain Zero Trust.

Easily Attain and Maintain
Least Privilege Access in Active Directory
All building blocks of organizational cyber security i.e. accounts, credentials and groups are stored in Active Directory, so attaining and maintaining least privilege access (LPA) in Active Directory is paramount to organizational cyber security.
To attain and maintain LPA in Active Directory (AD), organizations, first and foremost, need to be able to accurately assess who has what access in AD, because to lock-down access, one first needs to know who has what access.
Unfortunately, there exist thousands of complicated security permissions (e.g. explicit, inherited, allow, deny, object-specfic, special rights etc.) in every Active Directory and they make it very difficult to accurately assess who currently has what access, in turn making it very difficult to lock-down access, and thus to attain and maintain LPA in Active Directory.
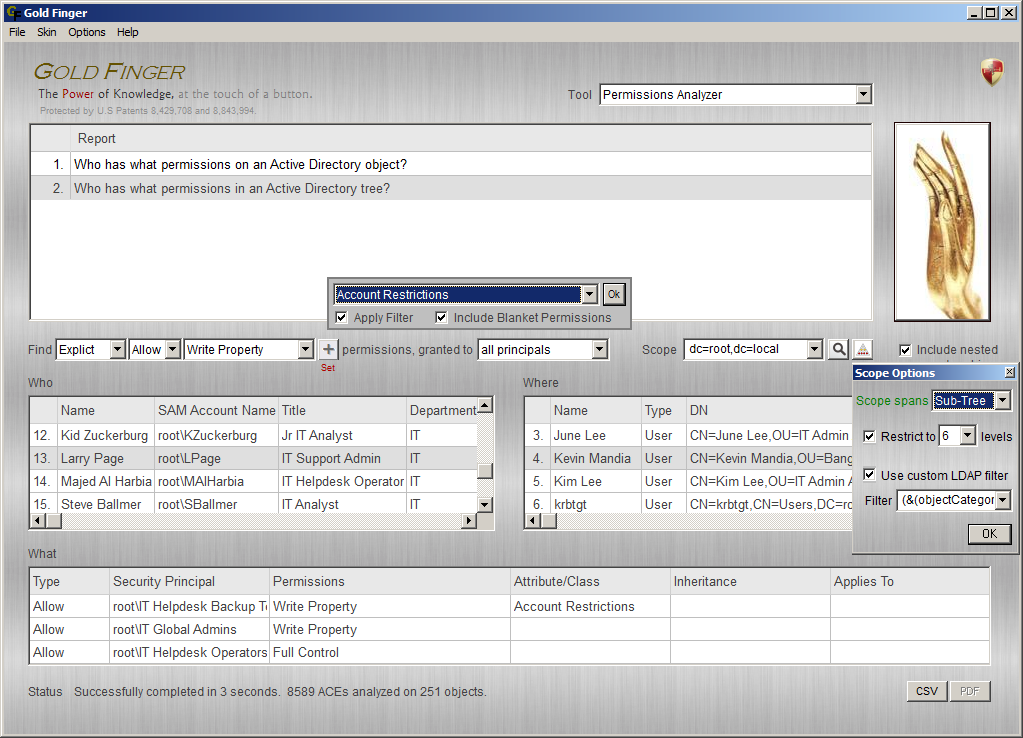
Our unique, Microsoft-endorsed Gold Finger solution can instantly, automatically and accurately determine who currently has what access, domain-wide, on all (thousands of) Active Directory objects, based on the accurate determination of effective permissions, thereby solving the problem of determining who actually has what access in Active Directory.
It also identifies and pinpoints the exact underlying permissions and group memberships that enable all identified access.
Thus, by automating the accurate assessment of who has what access, where and how, domain-wide in Active Directory, it lets organizations easily assess and lockdown access, and thus easily attain and maintain LPA in Active Directory.
Gold Finger
Gold Finger is the world's only cyber security solution that can accurately, automatically and instantly assess (identify) exactly who has what privileged access, where and how, including delegated administrative privileges, domain-wide, uniquely empowering organizations to easily attain and maintain least privilege access in Active Directory.
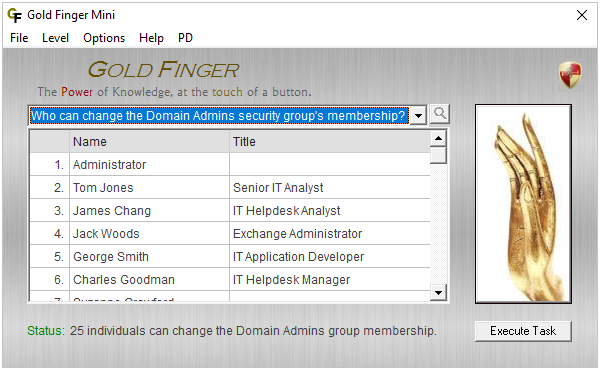
Gold Finger Mini
Gold Finger Mini is the world's only privileged access audit tool for Active Directory that enables everyone in the world to instantly find out exactly who has the most powerful privileged access in any Active Directory domain in the world.
Mission-critical Active Directory Privileged Access Insights
Organizations that operate on Active Directory and do not have exact answers
to the following 7 questions, remain substantially vulnerable -
- Who can run Mimikatz DCSync against your Active Directory?
- Who can modify the ACL protecting the AdminSDHolder object in Active Directory?
- Who can change the membership of all Domain Admins equivalent privileged security groups?
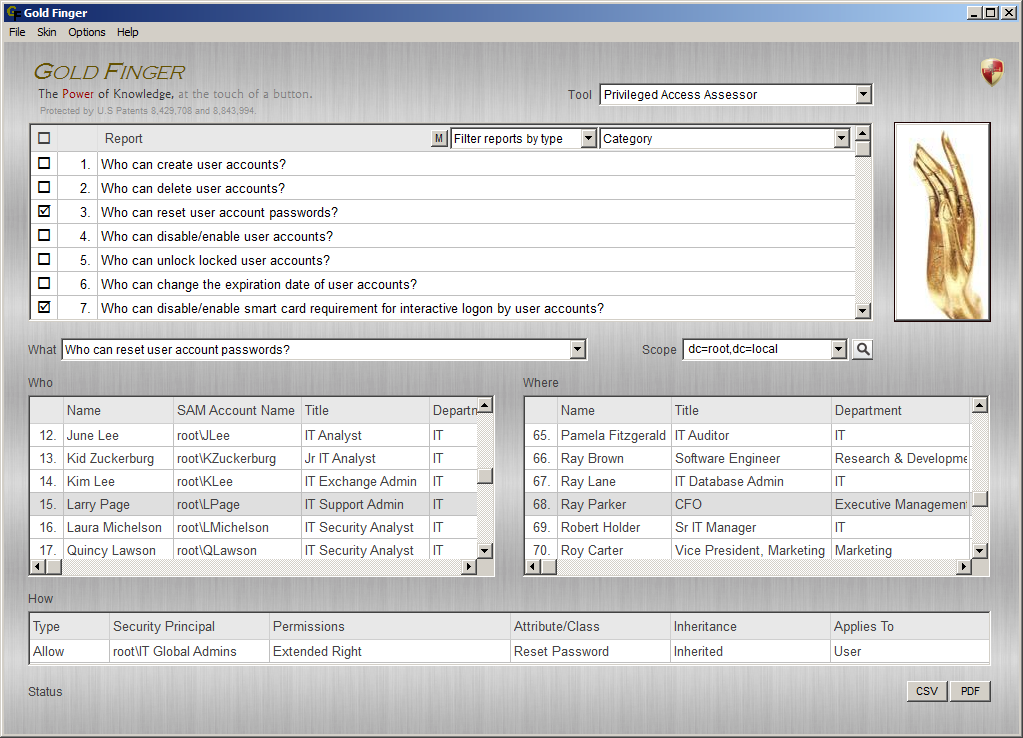
- Who can reset the passwords of privileged, executive and high-value user accounts in Active Directory?
- Who can create, manage/control and delete accounts, groups and organizational units (OUs) in Active Directory?
- Who can change privileged access in Active Directory to instantly obtain access to millions of organizational IT resources?
- Who can compromise Active Directory integrated apps/services (e.g. Azure Connect) by modifying Active Directory contents?
There is one and only one correct way to accurately assess exactly who has what privileged access in Active Directory,
and only* our unique, Microsoft-endorsed Gold Finger and Gold Finger Mini privileged access audit solutions can do so.
* If your existing tools merely rely on determining "Who has what permissions in Active Directory," you're likely operating on dangerously inaccurate insights.

Fulfilling A Paramount Need
Organizations have a paramount cyber security need to be able to accurately* assess and lockdown exactly who has what privileged access, where and how in their Active Directory based hybrid networks, to -
Attain and Maintain Zero Trust
Audit and Secure Active Directory
Perform Privileged Account Discovery
Implement Privileged Access Management
Attain and Maintain Least Privilege Access
Securely Manage Identities and Access in AD
Gain High-Value Active Directory Threat Intelligence
Manage Risk and Demonstrate Regulatory Compliance
Our Microsoft-endorsed Gold Finger tooling uniquely* empowers organizations worldwide to fulfill this paramount need.
* Based on accurate effective permissions analysis
We Accurately Assess (Identify) who has
Privileged Access in Active Directory
Privileged Access (i.e. unrestricted & delegated administrative privileges,) is the new holy grail for perpetrators and the #1 target in organizational cyber security.
At 85% of organizations worldwide, the proverbial Keys to the Kingdom, i.e. the most powerful Domain Admin level privileged access, and the vast majority of delegated administrative privileges, reside inside their Active Directory.
In the SolarWinds Breach, the Colonial Pipeline Hack, the Okta Breach and every major breach in the last decade, perpetrators targeted and compromised just 1 AD privileged user account, then used it to inflict colossal damage.
The single most important and effective cyber security measure organizations can enact to prevent breaches is to accurately identify (i.e. assess) and minimize (i.e. lock-down) privileged access (i.e. both unrestricted and delegated administrative privileges,) in Active Directory.
Our Microsoft-endorsed solutions uniquely enable and empower organizations worldwide to accurately and instantly assess (i.e. identify), and subsequently minimize and maintain locked-down privileged access in Active Directory.
Only Our Solutions Accurately Assess
Privileged Access in Active Directory
The need to know exactly who has what privileged access, where and how in Active Directory, at all times, is paramount.
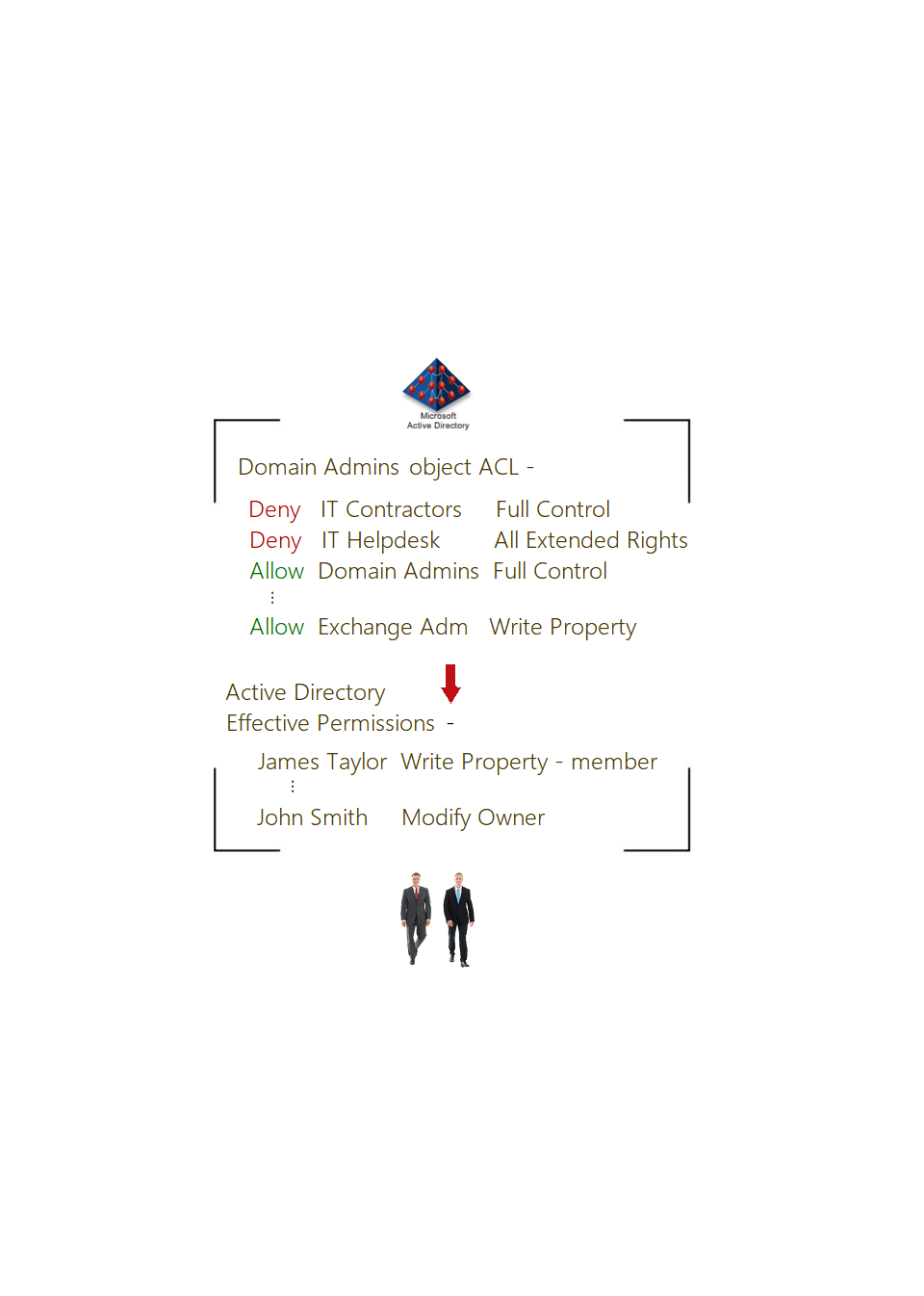
Active Directory's security model lets organizations precisely delegate privileged access (i.e. administrative privileges), but it makes it very difficult to accurately audit privileged access, especially to audit delegated administrative privileges.
In every AD, there are thousands of allow, deny, explicit and inherited security permissions, granted to users and groups, and together they impact the actual (effective) access, making it very difficult to accurately audit privileged access.
Most organizations and solutions do not know this fact, and determine "Who has what permissions in Active Directory," which is incorrect and delivers vastly inaccurate results, reliance upon which leaves them substantially vulnerable.
There is only one correct way to accurately assess (i.e. identify) privileged access in Active Directory, and that is by accurately determining "Who has what effective permissions in Active Directory?"
Only our Microsoft-endorsed Privileged Access Assessment products can accurately determine effective permissions in AD, and thus only our products can accurately assess privileged access in AD.

We Deliver Instant, Accurate Privileged Access Insights
There is only one way to accurately assess privileged access in Active Directory and that involves accurately determining effective permissions on Active Directory objects.
Our Active Directory Privileged Access Assessment tools are the world's only tools that can accurately calculate effective permissions to accurately determine who has what privileged access in AD.
Our tools can uniquely accomplish the remarkable technical feat of being able to automatically and accurately determine effective permissions on thousands of Active Directory objects, and determine what administrative privileges (tasks) they entitle, letting organizations accurately assess all privileged access in AD.
Our tools also identify the exact underlying security permissions that enable such privileged access, empowering organizations to quickly and easily lockdown privileged access in Active Directory.
Our tools thus deliver instant, accurate privileged access insights and uniquely empower organizations to find out exactly who has what privileged access in Active Directory, where and how.

Eliminate The World's #1 Attack Vector
Active Directory Privilege Escalation poses the world's #1 cyber security risk and is the world's #1 attack vector because it clearly and directly threatens the foundational security of over 85% of organizations worldwide.
It can be easily exploited to compromise the security of virtually everything in Active Directory, including any domain user account, computer account, security group, OU etc., and particularly all-powerful Active Directory privileged user accounts and security groups, as well as high-value targets such as AzureADConnect that enable Cloud integration.
Fact - In virtually ever major cyber security breach, including the SolarWinds Breach, Colonial Pipeline Hack, Okta Breach and others, perpetrators targeted, compromised and misused a single Active Directory privileged user account to gain unrestricted system-wide access and inflict colossal damage.
Our Microsoft-endorsed Gold Finger solution uniquely empowers organizations to accurately and quickly identify and lockdown all excessive/unauthorized privileged access in Active Directory, enabling them to virtually eliminate the #1 attack vector to organizational cyber security.
Our Gold Finger Suite of Active Directory Privileged Access Assessment Tools
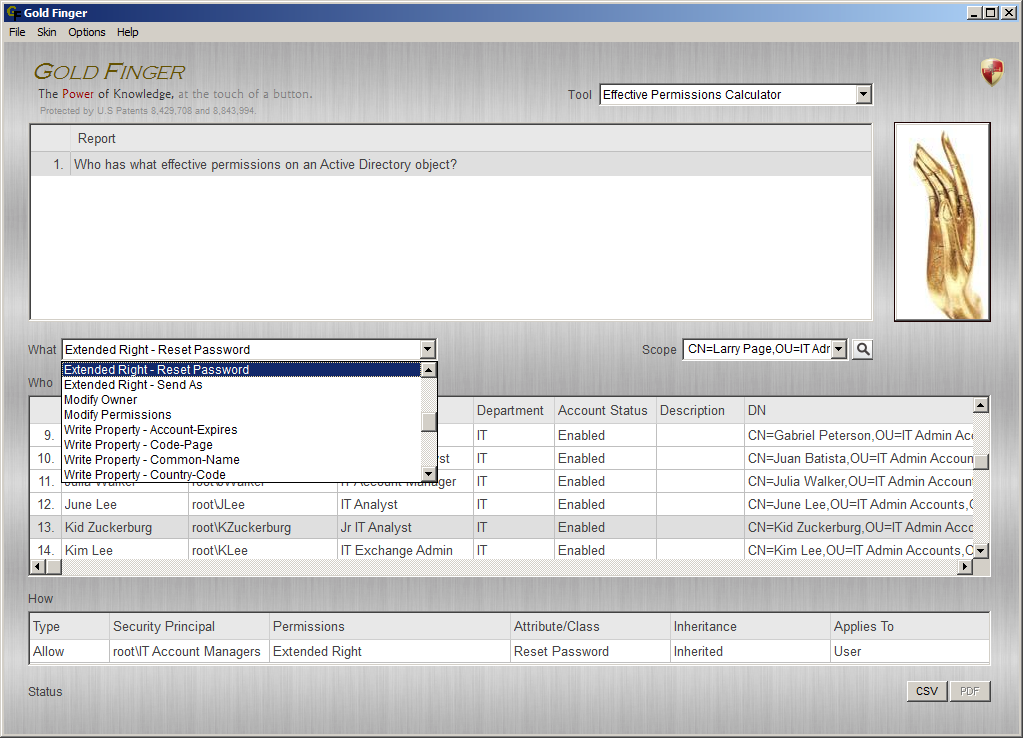
Active Directory Effective Permissions Calculator
Calculate "Who has what effective permissions in Active Directory?"
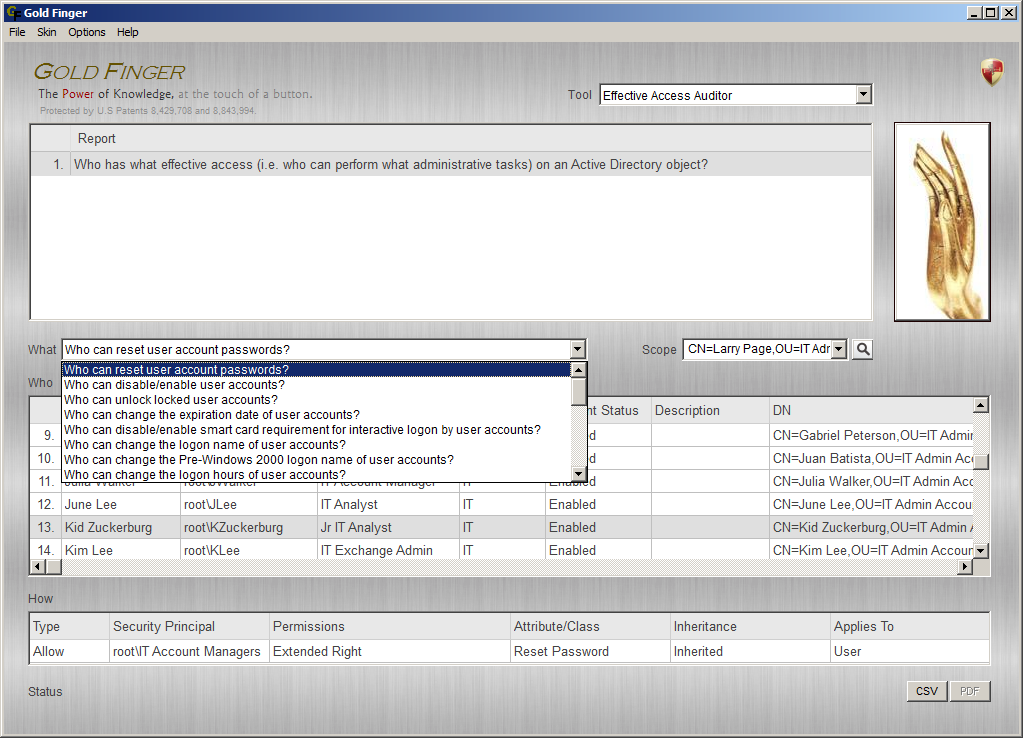
Active Directory Effective Access Auditor
Audit "Who has what effective access in Active Directory?"
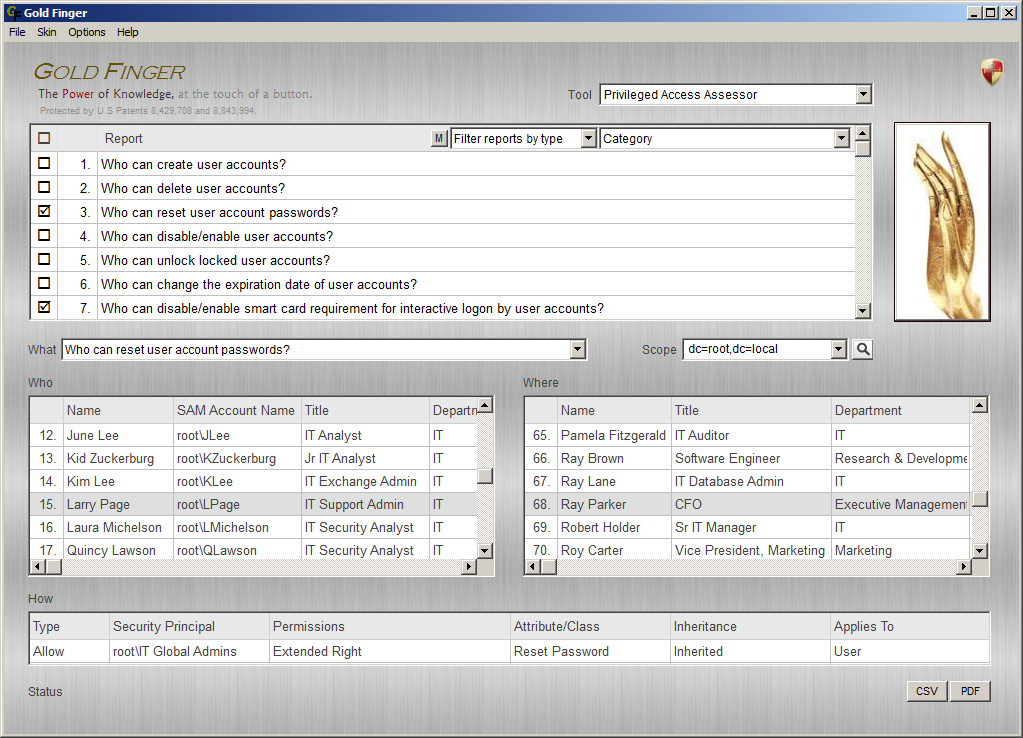
Active Directory Privileged Access Assessor
Assess "Who has what privileged access domain-wide in Active Directory?"

Start Here
If you are an Active Directory or Cyber Security professional,
allow us to help you quickly find what you may be looking for.
I need to -
Our Microsoft-endorsed Gold Finger can do all this at a button's touch.
Our Global Customers