Celebrating Eighteen
We are celebrating eighteen years in business and giving away up to $100M of our unrivaled Gold Finger access assessment software for Active Directory to organizations worldwide.
Details below.

We are Paramount Defenses
Microsoft Active Directory is the foundation of IT, cyber security and privileged access at 85% of organizations worldwide.
Paramount Defenses was founded on Mar 14, 2006 by former Microsoft Program Manager for Active Directory Security.
We possess unrivaled Microsoft-endorsed capability and expertise in Privileged Access Assessment in Active Directory, i.e. the ability to accurately assess exactly who has what access in Active Directory, an absolutely paramount necessity, without which not a single Active Directory object and no Active Directory deployment in the world can be secured.
Over the years, we have helped secure some of the world's most important business and government organizations, including the U.S. Treasury, the U.S. Department of Defense, the British Government, Canadian Defense Forces, the Saudi Arabian Government, several Fortune 100 companies and many other organizations across six continents.
Gold Finger
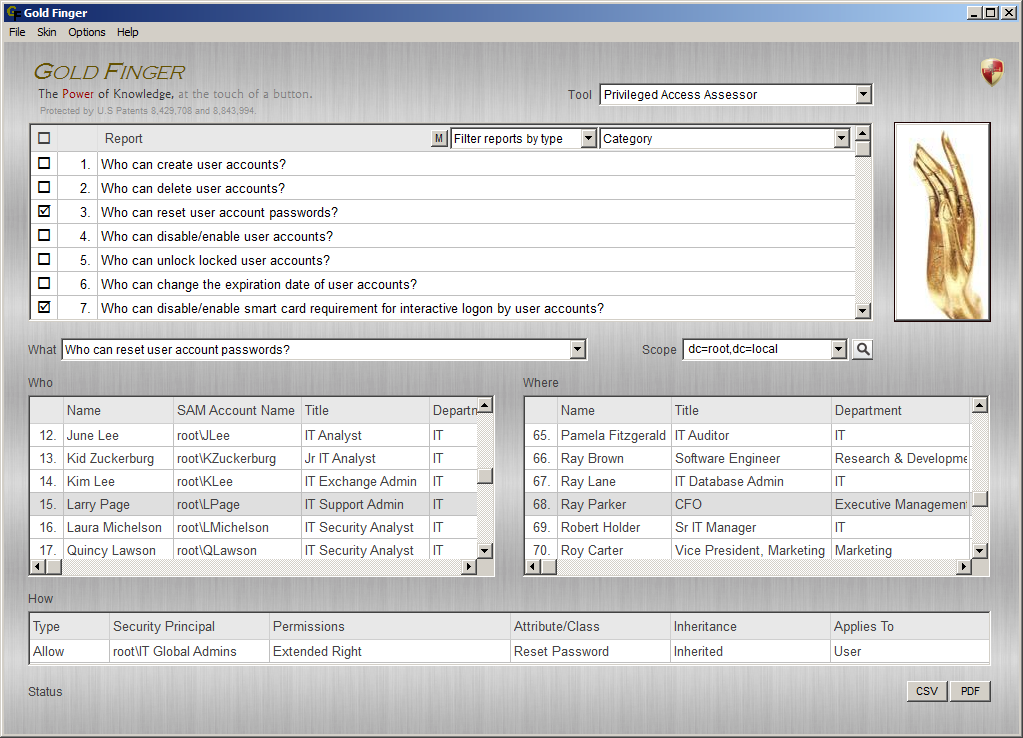
Our flagship Microsoft-endorsed Gold Finger privileged access assessment solution is the only cyber security solution in the world that can accurately determine effective permissions /effective access in Active Directory (AD) deployments.
Simply put, only Gold Finger can accurately assess who has what access (, incl. privileged access) in Active Directory.
Today there are many solutions that claim to be able to help assess/audity/identify privileged access in Active Directory, but they all fundamentally rely on determining "who has what permissions in Active Directory," which only yields inaccurate results, reliance upon which could result in a serious and possibly colossal cyber security breach.
There is one and only one correct way to accurately determine who has what access in Active Directory and that is by determining "who has what effective permissions in Active Directory," and only Gold Finger can do so accurately.
Only Gold Finger's accurate patented access assessment capabilities can correctly analyze security permissions in Active Directory and accurately assess exactly who has what privileged access, where and how, in Active Directory.
Accurate Access Assessment is Paramount
Today, every organization operating on Active Directory must know exactly* -
- Who can run Mimikatz DCSync against their Active Directory?
- Who can modify the ACL protecting any and every object in Active Directory?
- Who can change the membership of any and all security groups in Active Directory?
- Who can link a malicious GPO to any and all OUs in Active Directory to unleash ransomware?
- Who can reset the passwords of any and all regular and privileged user accounts in Active Directory?
- Who can disable the use of Smartcards for interactive logon on all domain user accounts in Active Directory?
- Who can create, manage/control and delete accounts, groups and organizational units (OUs) in Active Directory?
- Who can change the membership of any and all security groups (e.g. Confidential Access Group) in Active Directory?
- Who can change privileged access in Active Directory to instantly obtain access to millions of organizational IT resources?
- Who can compromise Active Directory integrated apps/services (e.g. Azure Connect) by modifying Active Directory contents?
* If your existing tools merely rely on determining "Who has what permissions in Active Directory," you're likely operating on dangerously inaccurate insights.

$100 Million* Giveaway
Founded in 2006, we are pioneers in access assessment, and with our laser focus on Active Directory, we have had the privilege of demonstrating thought and industry leadership in this vital area of organizational cyber security for 18 years.
To celebrate eighteen years in business, this year we are giving away up to $100 Million* of our flagship Gold Finger access assessment software for Active Directory, to all organizations that can affirmatively answer 1 simple question –
Question - Can the solution your organization uses today to assess access in Active Directory match the accuracy of Gold Finger's Active Directory Effective Permissions Calculator or Active Directory Privileged Access Assessor?
Every organization in the world whose answer to this 1 simple question is a provable* Yes, can request and receive* a free one-year license of our corresponding Gold Finger tooling, ranging in value from US $ 25,000 up to US $ 250,000.
Simply stated, if your existing solution can match the accuracy of the world's only accurate access assessment solution for Active Directory, then you can have Gold Finger, i.e. the world's gold standard for AD access assessment, for free.
* Subject to the Terms and Conditions of our giveaway, as stated below.

Why Accuracy Matters
In case you're wondering as to why we're making this generous offer, it is cardinally to help all organizations worldwide understand the paramount importance of accuracy in securing access, particularly privileged access, in Active Directory, and to help them realize that whatever tooling they're using today is very likely (99.9%) not providing accurate insights.
Accuracy in access assessment is paramount because a single i.e. just one bit change, password reset, membership change, GPO link, ACL change etc. in Active Directory could instantly grant a perpetrator the "Keys to the Kingdom".
Today, there exists an ocean of excessive unidentified privileged access in almost every Active Directory in the world, which until accurately assessed and then locked-down, poses a clear and present danger to organizational security.
Fact - In virtually every major breach of the last two decades, perpetrators first targeted and gained privileged access in Active Directory, i.e. the proverbial "Keys to the Kingdom" and then easily proceeded to swiftly inflict colossal damage.
If this fact is not enough, we also possess sufficient operational expertise to be able to easily demonstrate the enactment of this serious risk in the foundational Active Directory of any organization in the world that wishes to see it demonstrated.
Popular Solutions used for Access Assessment in Active Directory
Here is a helpful list of various available solutions used by organizations in their efforts to try and assess who has what access, including privileged access, in Active Directory today (, listed in random order) -
CrowdStrike Falcon Identity Protection (CrowdStrike)
Bloodhound (SpectreOps)
Ping Castle (Ping Castle)
Directory Services Protector (Semperis)
BeyondTrust Auditor (BeyondTrust)
Purple Knight (Semperis)
Enterprise Reporter for Active Directory (Quest)
Effective Permissions Reporting Tool (ManageEngine)
Active Directory Permissions Reporting Tool (ManageEngine)
Permissions Analyzer for Active Directory (SolarWinds)
Singularity (Sentinel One)
Identity Exposure (Tenable)
We trust that organizations understand English, as they consider our use of the term "only" as used above, and we invite all organizations to compare the accuracy of any of these tools with that of our Gold Finger.
AD Secure (Attivo Networks)
AD Assessor (Attivo Networks)
Hyena (SystemTools)
Lepide Auditor (Lepide)
AclDiag (Microsoft)
ACLight (CyberArk)
PowerShell for Active Directory (Microsoft)
ADACLScanner (Robin Granberg)
AD Permissions Reporter (CJWDev)
dsacls (Microsoft)
IdentityIQ (SailPoint)
StealthAudit Active Directory Permissions Analyzer (StealthBits)

You're Invited
We cordially invite all organizations worldwide that operate on Active Directory today to take us up on our generous offer.
To do so –
Read The Paramount Brief
Understand Active Directory Effective Permissions
Try the free version of Gold Finger Mini to verify it works.
Request and obtain a free 14-day Gold Finger evaluation.
Compare the accuracy of your existing solution with that of Gold Finger, and if they match, let us know.
Alternatively, we can walk you through the entire process –
Our offer could save your organization over US $100,000 in IT spending each year, but far more importantly, it could help your organization accurately assess and lockdown privileged access, domain-wide, in its foundational Active Directory.
NOTE - Our offer is limited to the first 1000 companies (from 100+ countries worldwide) that can provably demonstrate an accuracy match of their existing solution with Gold Finger, on a first-come-first-serve basis, and subject to no more than 50 awardee organizations from any one country.

*Giveaway Terms and Conditions
Paramount Defenses will give away up to a total of US $ 100 Million in single one-year term-use organization-specific licenses of our Gold Finger software, at our sole discretion and subject to the terms below, during the six-month period from March 15, 2024 through September 15, 2024 –Any business or government organization that operates on Microsoft Active Directory can apply to participate in our software license giveaway. For security reasons, we are unable to extend participation to vendors of various existing Active Directory access assessment solutions.
A participating organization must be able to demonstrably prove that their existing solution can match the accuracy of our Gold Finger solution.
Proof of an existing solution being able to match the accuracy of Gold Finger must be demonstrated in a real-world production Active Directory.
The real-world production Active Directory used to demonstrate the accuracy match must involve the use of both Allow and Deny permissions, Explicit and Inherited permissions, with access specified for accounts, well-known security principals and nested and circularly nested groups.
To demonstrate an accuracy match, a participating organization will only need to demonstrate to Paramount Defenses personnel that the results of ten specific assessments made using the organization's existing solution match the results of the same assessments made by Gold Finger. E.g. Exactly who is effectively allowed Reset Password extended right on the CEO's account, Who can create user accounts in the domain etc.
In the event that a participating organization is able to demonstrate an accuracy match, the complimentary organization-specific license of Gold Finger tooling that will be gifted will be that of the specific Gold Finger tooling against which the accuracy claim has been demonstrated.
To participate, an organization must 1) have read and understood The Paramount Brief, 2) understand Active Directory Effective Permissions, 3) try the free version of Gold Finger Mini to verify that Gold Finger works in their environment, and then 4) request a complimentary evaluation of Gold Finger in a real-world environment so as to be able to make a comparison to their existing Active Directory access assessment solution.
This offer will be limited to the first 1000 companies (from 100+ countries worldwide) that can provably demonstrate an accuracy match of their existing solution with Gold Finger, on a first-come-first-serve basis, and subject to no more than 50 awardee organizations from any one country.
Our Global Customers




















